AWS IoT Tunnel Example: A Comprehensive Guide To Secure Device Communication
Amazon Web Services (AWS) IoT Tunnel provides a secure and efficient way to establish communication between IoT devices and external applications. As IoT continues to expand across industries, ensuring secure and reliable device management has become critical. This article delves into the importance of AWS IoT Tunnel, its functionalities, and how it can be implemented effectively.
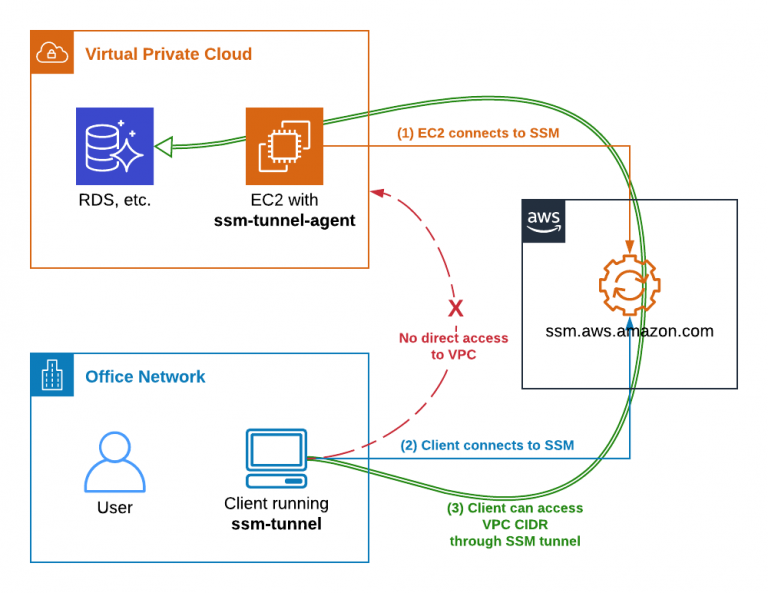
AWS IoT Tunnel enables you to connect to IoT devices that are behind a firewall or NAT without requiring permanent open ports. This makes it an ideal solution for scenarios where devices are located in restricted networks. Whether you're managing industrial equipment, home automation systems, or healthcare devices, AWS IoT Tunnel ensures secure and seamless communication.
In this comprehensive guide, we will explore the technical aspects of AWS IoT Tunnel, provide real-world examples, and discuss its implementation steps. By the end of this article, you will have a clear understanding of how AWS IoT Tunnel works and how it can enhance your IoT infrastructure.
Read also:Revitalize Your Wellness Journey With Core Life Smoothies
Table of Contents
- Introduction to AWS IoT Tunnel
- Why Use AWS IoT Tunnel?
- AWS IoT Tunnel Architecture
- Setting Up AWS IoT Tunnel
- Real-World AWS IoT Tunnel Example
- Security Features of AWS IoT Tunnel
- Common Use Cases
- Troubleshooting AWS IoT Tunnel
- Best Practices
- Conclusion
Introduction to AWS IoT Tunnel
AWS IoT Tunnel is a service designed to facilitate secure communication between IoT devices and external applications. It allows you to establish a secure tunnel to devices that are located behind firewalls or NATs, without requiring permanent open ports. This feature is particularly useful for managing devices in restricted environments.
The tunneling mechanism ensures that only authorized users can access the devices, enhancing security while maintaining ease of use. AWS IoT Tunnel is part of the broader AWS IoT suite, which includes services like AWS IoT Core, AWS IoT Device Management, and AWS IoT Analytics.
Key Features of AWS IoT Tunnel
- Secure communication through encrypted tunnels
- No need for permanent open ports on devices
- Supports both TCP and UDP protocols
- Integration with AWS IoT Core for device management
Why Use AWS IoT Tunnel?
There are several reasons why AWS IoT Tunnel is an excellent choice for IoT device management:
Firstly, it enhances security by ensuring that devices are not exposed to the internet through open ports. Instead, it uses a secure tunneling mechanism that restricts access to authorized users only. This is crucial for protecting sensitive data and preventing unauthorized access.
Secondly, AWS IoT Tunnel simplifies the management of IoT devices. It allows you to connect to devices located in restricted networks without the need for complex network configurations. This makes it an ideal solution for enterprises that manage large fleets of IoT devices.
AWS IoT Tunnel Architecture
The architecture of AWS IoT Tunnel is designed to provide a secure and efficient way to establish communication between devices and applications. It consists of several components, including:
Read also:Aishah S A Comprehensive Guide To Her Life Career And Achievements
- AWS IoT Core: Acts as the central hub for device communication
- Tunnel Manager: Manages the creation and termination of tunnels
- Tunnel Proxy: Facilitates communication between the device and application
When a tunnel is established, the device and application communicate through the tunnel proxy, which ensures that all data is encrypted and secure. This architecture allows for seamless communication while maintaining high levels of security.
Setting Up AWS IoT Tunnel
Setting up AWS IoT Tunnel involves several steps, including configuring AWS IoT Core, creating a tunnel, and establishing a connection between the device and application.
Step 1: Configure AWS IoT Core
Before setting up AWS IoT Tunnel, you need to configure AWS IoT Core. This involves creating a thing, defining policies, and setting up certificates for device authentication.
Step 2: Create a Tunnel
Once AWS IoT Core is configured, you can create a tunnel using the AWS CLI or AWS Management Console. The tunnel creation process involves specifying the target device and defining the tunnel's parameters.
Step 3: Establish a Connection
After the tunnel is created, you can establish a connection between the device and application. This involves configuring the device to connect to the tunnel proxy and ensuring that the application can communicate with the device through the tunnel.
Real-World AWS IoT Tunnel Example
Let's consider a real-world example of how AWS IoT Tunnel can be used in a manufacturing environment. Imagine a factory that uses IoT sensors to monitor equipment performance. These sensors are located behind a firewall, making it challenging to access them remotely.
By using AWS IoT Tunnel, the factory can establish a secure connection to the sensors without requiring permanent open ports. This allows engineers to remotely monitor and troubleshoot equipment, improving operational efficiency and reducing downtime.
Steps to Implement AWS IoT Tunnel in a Manufacturing Environment
- Install AWS IoT Core on the factory's network
- Create a tunnel for each sensor that needs remote access
- Configure the sensors to connect to the tunnel proxy
- Grant engineers access to the tunnel through the AWS Management Console
Security Features of AWS IoT Tunnel
AWS IoT Tunnel incorporates several security features to ensure that device communication is secure and protected. These features include:
- End-to-end encryption for all data transmitted through the tunnel
- Authentication and authorization mechanisms to restrict access to authorized users
- Regular security updates and patches to address vulnerabilities
These security features make AWS IoT Tunnel a trusted solution for enterprises that require high levels of security for their IoT devices.
Common Use Cases
AWS IoT Tunnel can be used in various industries and applications. Some common use cases include:
Remote Device Management
In scenarios where devices are located in remote or restricted environments, AWS IoT Tunnel allows for secure and efficient device management. This is particularly useful for industries like oil and gas, where equipment is often located in remote locations.
Healthcare Device Monitoring
In the healthcare industry, AWS IoT Tunnel can be used to monitor medical devices remotely. This ensures that patients receive timely care and that medical staff can respond to emergencies quickly.
Home Automation
For home automation systems, AWS IoT Tunnel provides a secure way to connect smart devices to external applications. This allows homeowners to control their devices remotely while maintaining high levels of security.
Troubleshooting AWS IoT Tunnel
While AWS IoT Tunnel is a robust solution, issues may arise during implementation. Common troubleshooting steps include:
- Verifying device certificates and policies
- Checking network configurations and firewall settings
- Reviewing logs for error messages
By following these steps, you can identify and resolve issues quickly, ensuring that your IoT infrastructure remains operational.
Best Practices
To ensure the successful implementation of AWS IoT Tunnel, consider the following best practices:
- Regularly update device firmware and software
- Monitor tunnel activity and usage
- Implement strong authentication and authorization mechanisms
By adhering to these best practices, you can maximize the benefits of AWS IoT Tunnel and ensure that your IoT devices remain secure and efficient.
Conclusion
AWS IoT Tunnel is a powerful tool for secure IoT device communication. It provides a reliable and efficient way to establish connections between devices and applications, even in restricted environments. By following the steps outlined in this guide, you can successfully implement AWS IoT Tunnel and enhance your IoT infrastructure.
We encourage you to share your thoughts and experiences with AWS IoT Tunnel in the comments section below. Additionally, feel free to explore other articles on our site for more insights into IoT and cloud computing. Together, let's build a more connected and secure future!
References:
Article Recommendations